Our Products
AI powered Consent Management System and Data Erasure System
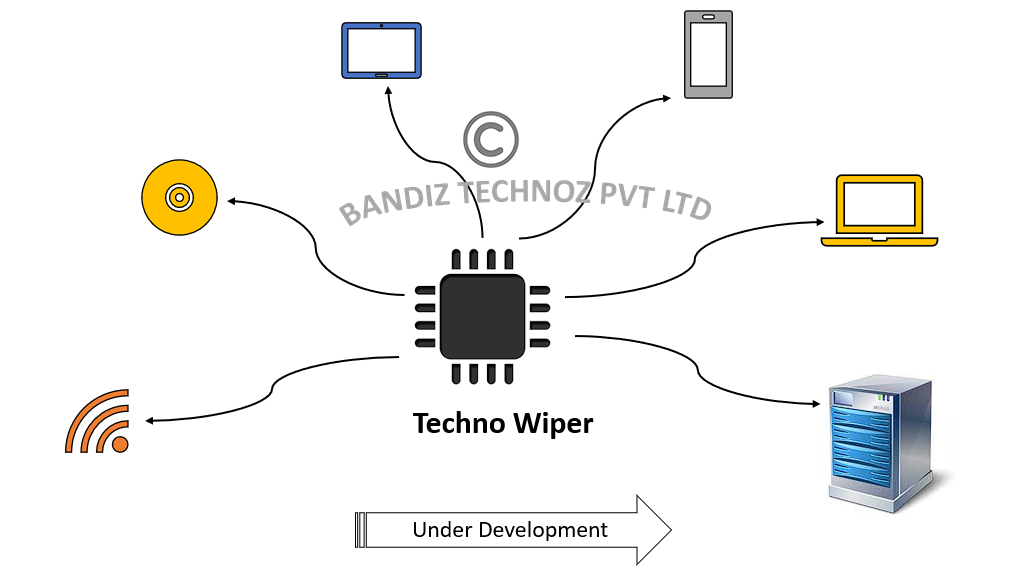
TechnoWiper
CPS system , adds value to the industries, corporates and even individuals, when it comes to data destruction. Powered by AI, it can auto detect type of devices and suggest appropriate wiping action. With myriad of features ranging from offline to online.
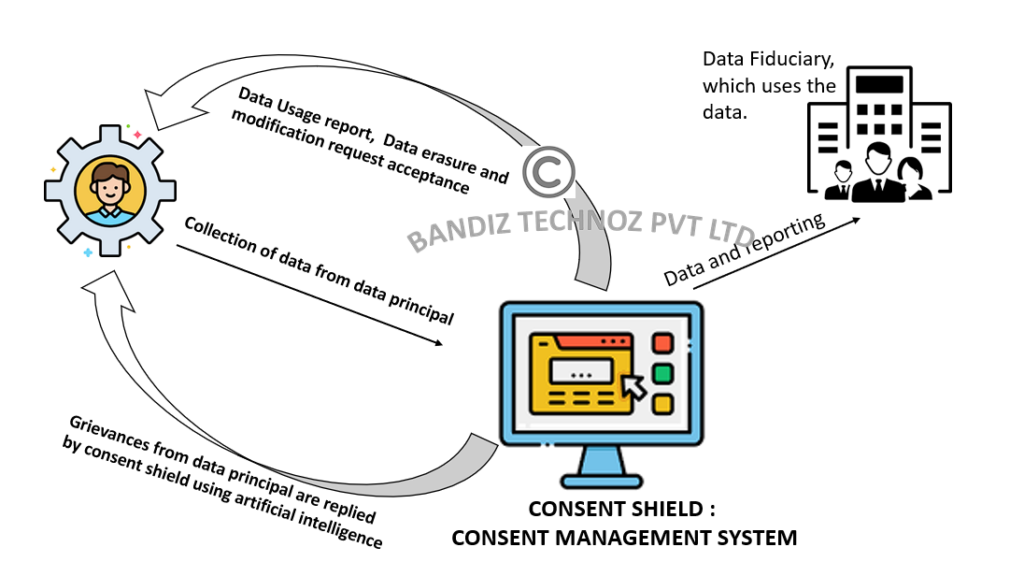
Consent Shield
Consent Shield collects data from data principal, manages data securely within organization, but sharing datakey, instead of real data with other entities in organization. It has AI powered response system to handle grievances, modification request as as wiping requests.
Indian Data Protection Bill
What are the key provisions of the Data Protection Bill?
- Businesses are required to provide a detailed notice to individuals from whom they are collecting data. This notice must be written in clear and understandable language, outlining the types of personal data being collected and the purposes for processing such data.
- Businesses must designate a data protection officer, whose name must be included in the data consent form. Individuals have the right to withdraw their consent for data processing at any time.
- If an individual is dissatisfied with a business's response to their queries regarding data collection, or if they receive no response within a specified period (usually seven days or as prescribed), they have the option to file a complaint with the Data Protection Board according to prescribed procedures.
- Organizations failing to prevent data breaches may face penalties as outlined in the legislation.
Responsibilities of Indian Enterprises
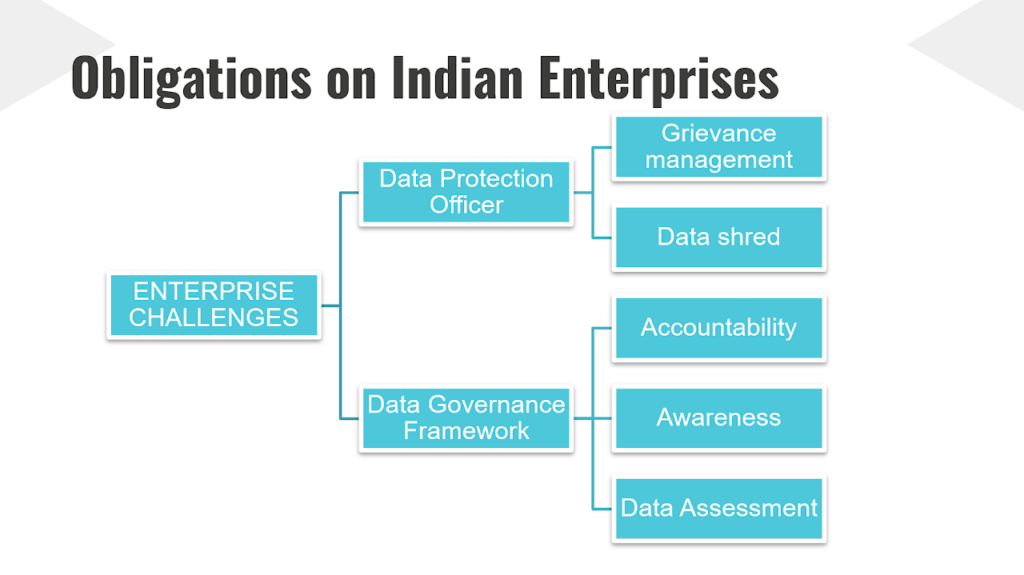
Indian Business Requirements:
- Understanding and Adhering to Data Protection Laws
- Implementation of Robust Data Management Systems
- Regular Audits and Assessments
- Employee Training and Awareness Programs
- Collaboration with Regulatory Authorities
Data Compliance Service Offering
Access within organization
Data protection officer
Communications
Breach Protection
Usage Information
Data Shredding
Process
Cybersecurity : Evergrowing Market
The Expanding Realm of Cybersecurity: Market Trends and Projections

Market Growth
The cybersecurity sector has witnessed substantial expansion, reaching USD 182.86 billion in 2023, with projections indicating further growth to exceed USD 314.28 billion by 2028, reflecting a significant CAGR of 11.44%.
Key Drivers
Expansion is fueled by heightened cyber threats and increased awareness of digital security’s significance among organizations and individuals.

Technological Advancements
Innovations such as artificial intelligence, machine learning, and advanced encryption are revolutionizing cybersecurity, enabling more robust defense mechanisms against evolving threats across diverse sectors.
USP : What Sets Us Apart?
Certified Professional
We will employ certified professionals , who have
established themselves in data protection field. We will
pik up resources which are certiefied CIPP, ISO 27001
Lead Auditor, GDPR practitioner or CISA.
Experience of
Founders
Founders have more than 20 years of
experience , with one of the founder
having worked as Lead auditor in US
as well as Europe for nearly a
decade.
AI Empowerment Solutions
Threat detection — Pattern analysis to identify potential threat.
Bahavioural analaysis — deviations from baseline can reflect
unauthorized access.
Malware detection — Machine learning models can classify and
quarantine suspicious files or activities.
Vulnerability –- scan software code
Compliance + Dark
data migration
We will employ certified professionals , who have
established themselves in data protection field. We will
pik up resources which are certiefied CIPP, ISO 27001
Lead Auditor, GDPR practitioner or CISA.
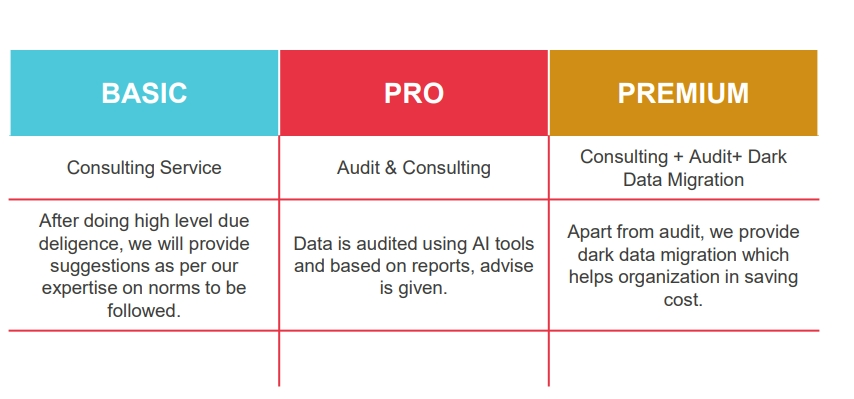
Types Of Services Offered